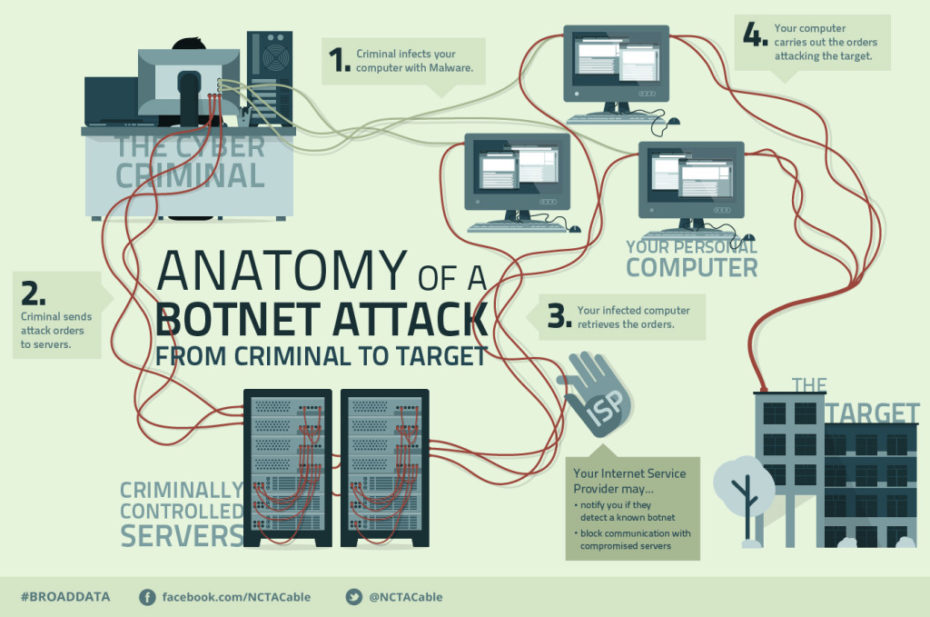
Traffic jams are caused when too many cars all try to go to the same place at the same time. The roads are overwhelmed, traffic comes to a standstill, and no one gets to their destination on time. A distributed denial of service (DDoS) cyberattack works the same way. Someone purposely forces too many bits of information to a server all at once, rendering it functionless. The system is overwhelmed. In late March, Spamhaus, an organization based in Europe dedicated to tracking Internet spammers, was hit with the largest DDoS attack in history. The alleged responsible party, CyberBunker, had been listed by Spamhaus as a source of spam. CyberBunker was angry about what it considered to be an illegitimate blacklisting and as retaliation, attacked Spamhaus with a massive flood of 300Gbps of data, making the system unavailable.
The chart above shows how a DDoS attack like the one delivered to Spamhaus can work. It’s a surprisingly simple concept that, when executed, hijacks a benign Internet lookup tool for its own nefarious purpose. For this particular attack the criminals first amassed a list of vulnerable computers and home routers that could be unwittingly tricked into carrying out a DDoS attack. In the case of Spamhaus, the attackers generally targeted off-the-shelf home routers and servers that were connected to home and corporate networks and were configured out-of-the-box to respond to all queries for web page addresses. After amassing a list of routers and computers that were susceptible to compromise, the cyber attacker was able to use the Internet directory system to launch the attack by falsely impersonating Spamhaus computers and by asking each of the open routers to send substantial data payloads to the Spamhaus IP addresses. The mass volume of sent data from tens of thousands of unwitting devices was amplified along the way and when it arrived at its destination, was so enormous that it overloaded the target servers and legitimate traffic was unable to access the site.
Attacks like this have the potential to relentlessly and indefinitely cause severe damage to businesses and governments and to indiscriminately affect websites other than the intended target. DDoS attacks are effective and efficient. But there are steps that users can take to protect their routers and computers from being hijacked. By reducing the vulnerability of your computer and ensuring that your routers and servers are properly configured, you can help protect them from being taken over and used in an attack.
In addition, our collective efforts to identify and respond to attacks such as these can be greatly aided by measures that support real-time sharing of information about cyber-threats. In the case of the Spamhaus attack, the coordinated sharing of information among all the parties affected could have reduced the impact of the attack or even prevented the attack. But because they failed to communicate, the attack went as planned and caused severe damage not just to Spamhaus, but because DDoS indiscriminately attack, to many other individuals and businesses. It seems logical that this kind of information should be shared, but today it often doesn’t occur due to legal uncertainties. This week the House of Representatives will consider the Cyber Intelligence Sharing and Protection Act, H.R. 624, which would allow organizations like tech companies, social media sites, and your ISP to share cyber-threat information to help better protect your data and the Internet’s infrastructure. By promoting more effective information sharing, efforts like this may be able to help mitigate and possibly prevent damage during a DDoS attack as well as identify the attacker.
In a connected world, all members of the Internet ecosystem share the responsibility of ensuring businesses, schools, governments, and individuals can work online safely. By opening channels of communication, establishing systems of knowledge sharing, and ensuring our homes and businesses are using secure devices, coordinated attacks like the DDoS attack on Spamhaus can be prevented.